Flush Those USB Drive Viruses Away
USB viruses are so common these days that people expect their USB drive to be infected when inserted into a public computer. Although vicious as these viruses may be, there are simple ways to prevent them from infecting your system. You can find more information by reading my blog, A New Virus Infection Method at Sonicsoft Wired.
Now, of course, occasionally your USB drive will become infected with these type of viruses. What ever shall we do? Luckily, I have created a simple survival guide so that at least you have a technical know how on how to drive those viruses away.
Your Best Defense
Your best defense? Know your system. I don't mean to actually know the technical specifications, but more on the software side - what operating system version and service pack you have, the programs you have installed, any protection software such as anti viruses and anti spywares installed, and the usual behaviour of your system.
Of course, a dead giveaway of a virus is when your system behaves weird or unexpectedly, such as, and more commonly, changed Windows Internet Explorer title bar (replacing Internet Explorer with a different value, like a website or a slogan). Others are more subtle, like running unknown programs in your system, or mysterious pop-ups or dialog boxes that displays garbage.
The best way to protect yourself from threats like USB viruses is to know your Task List. It is the list of all running programs you have in your system. You can see the Task List by opening the Windows Task Manager.
To open Task Manager, either:
- press CTRL + ALT + DEL all at the same time, known as the three-finger salute; or
- right-click a blank portion of the task bar, and select Task Manager
SIDEBAR: Processes and Programs are used
interchangeably and mean the same thing
When the Task Manger opens, select the Processes tab. This tab has the complete list of every single program or processes your system is currently running. It is imperative that you familiarize yourself with this list. I am not saying that you need to memorize the list, but it really helps.
The Task manager Processes tab contains certain columns worth mentioning. The first column Image Name is the process or program's executable file name. You will usually find the name followed by the extension .EXE as these are the common executable. Some may end with .COM, or .BAT. Another column is labeled User Name, indicates which user executed the process. Depending on your system, it will contain your log-in name, SYSTEM, LOCAL SERVICE, or NETWORK SERVICE. This column is also important, as viruses are run by your log-in name, not by the system, or any service. Lastly, the column labeled CPU indicates how much the processes is using your computer. The higher this number, the busier the process is.
You need to be familiar with the Image Name column. It gets easier, as certain names are really discernible based on your knowledge of what programs you have in your system. For example, the task labeled Winword.exe is clearly your Microsoft Word (a bad example. It's named Winword because the original name is called Word for Windows, hence WinWord), and other stuff like mspaint.exe is your Windows Paint program.
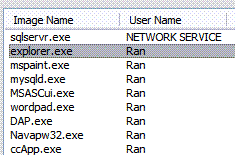
USB viruses are programs themselves, so they appear on your Task List. That's why you need to determine which process in the task list is legit, and which ones are viruses. To do that, carefully look through the list and see if any Image Name is unfamiliar. Since viruses are run by your local user name, you only need to look through processes with your user name under the User Name column. Be vigilant, as some viruses use file names that are surprisingly similar to legit programs, like explore.exe, or mpsaint.exe.
If you see any funny names (and that's why you need to be familiar with the list), do a web search on it. Chances are, they may be viruses. If a web search doesn't yield any results, immediately kill the process by hitting Del on your keyboard, or right-clicking the process and select End Process on the context menu. Standby if the process spawns again. If it does, look deeper in the task list - there might be another process that runs the virus every time it's terminated. If it doesn't, lucky for you. You can proceed to rooting it out.
Deleting Traces
Common USB viruses run by starting every time Windows starts. Of course, it can only start when the virus itself is present in your system, so you need to hunt down the root of the virus.
To do that, follow these steps:
- Open the Command Interpreter. Go to Start, then Run, type CMD and press enter. The Command Prompt will appear
- To go to the root of your drive, type CD \ (backslash) and press enter
- Type attrib and press Enter
- The program will list all the files on your root. Look carefully for a file name named AUTORUN.INF, which contains information about the virus. Your hard drive root shouldn't contain this file.
Before you delete this file, open it with Notepad. To do that, type:
attrib -h -r -s autorun.inf
and press Enter. Then type:
notepad autorun.inf
and press enter in the command prompt. Notepad will appear opening the file. Don't worry, it's safe to open this file.
Look through the contents of the file. Eventually, you'll find a line that goes:
open = someprogram.exe
inside. This is the Image Name of the virus. Now, make a mental note of the name, close Notepad, and go back to the command prompt. Type in the following:
attrib -h -r -s someprogram.exe
replacing the someprogram with the name you saw inside the notepad file. And press Enter. Then, type the following:
erase someprogram.exe
erase autorun.inf
pressing Enter after each line. This effectively removes the virus program from your computer. Depending on the number of drives you have, you will repeat the entire process (tedious, but required) to completely remove the virus, although you will have to change step 1 above with this step:
- Type in the drive letter of your next hard drive followed by a colon (D:) and press Enter. Proceed to step 2.
You will also have to do this on your USB drive.
Tweaking the Registry
We really removed the virus, but the changes the virus made to your system are still left. To do that, we need to tweak the registry.
IMPORTANT: TWEAKING THE REGISTRY IS VERY DANGEROUS AND MAY CAUSE IRREVERSIBLE DAMAGE TO YOUR COMPUTER. MAKE SURE YOU BACKUP YOUR REGISTRY FIRST, CREATE A RESTORE POINT, AND BE ABSOLUTELY CAREFUL. YOU ALSO NEED ADMINISTRATOR RIGHTS TO ACCESS THE REGISTRY. PLEASE SEARCH THE INTERNET FOR INSTRUCTIONS FOR BACKING UP AND RESTORING THE REGISTRY.
To open the Windows Registry Editor, go to Start, then Run. Type regedit and press Enter. You will enter the brain of Windows.
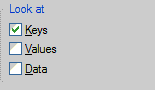
Press CTRL + F to do a search. Type mountpoints2 and press Enter. For faster results, make sure that only the Keys under Look at is checked. The Windows Registry will perform a search. After that, you will be presented with the result.
Alternatively, you can navigate to
MyComputer\HKEY_CURRENT_USER\Software\Microsoft\Windows
\CurrentVersion\Explorer\MountPoints2.
If you performed a search, make sure the status bar below is similar to this one.
Click an entry on the left, and check the properties on the right. If the right panel shows a _LabelFromReg Name, that's a hard drive attached to your computer. The value for this would be the label of your hard drive.
Now, expand the entry by clicking the [+] icon. The dead giveaway is that it has this plus icon. If it doesn't have the icon or it cannot be expand
If you expanded it and it contains the _AutoRun or AutoPlay node, yo
Now, search for other entries that is a drive and contains the _AutoRun node and perform the steps above.
You may also need to do this for your flash drives. It's quite tricky and complicated, but the idea is remove all _AutoRun entries except for CD drives. The hard part is figuring out which is which, so be careful. Don't do it if in doubt.
There you go, how to remove a virus info from your computer. It's quite complicated and tedious, but it's the only way if your anti virus cannot detect the virus. Also, be vigilant when inserting a foreign USB drive, and be careful.
For more questions, you can email me at wired.sonicsoft@gmail.com. I will reply to your questions as soon as possible.
Story:
Copyright 2007 Sonicsoft Corporation
All Rights Reserved




No comments:
Post a Comment